8 Best Practices for Securing User Data in Mobile Apps

Securing user data in mobile apps has become a critical concern in today's digital landscape. With the rise of mobile app usage, data security management has become a top priority for businesses and app developers. Unfortunately, mobile app security risks are also on the rise, as hackers find new ways to exploit vulnerabilities in mobile applications.
Organisations need to take measures to protect user data in their mobile apps. Check Point Research reported that 97% of organisations face a dramatic shift in mobile threats. What's more, nearly half of the organisations have employees who downloaded at least one malicious app. Plus, 40% of mobile devices remain vulnerable to cyber attacks. It's a severe concern for mobile app users who interact with businesses. They exchange data with brands on mobile apps without proper protection.
Apps without proper security measures are at risk of attacks, which can harm the business's reputation. Hackers can steal much access, such as:
- Steal user data.
- Intercept sensitive information that is travelling through the airwaves.
- Steal intellectual property and business assets.
- Steal identity to commit fraud.
So, developers and organisations should focus on eliminating security risks. Check out the best practices to ensure mobile app security.
What user data is classified as sensitive?
Many people store contacts, financial data, messages, photos, and medical history on their phones. This data is sensitive as it necessitates user consent to access it. Consequently, any data breach constitutes a serious security violation.
Spirion created five categories and sensitive user data information. These include:
- Data exposing racial, ethnic, political, and philosophical beliefs.
- Genetic and biometric data can identify an individual's identity.
- Health history data.
- Data about an individual's gender and sexual orientation.
Man-in-the-Middle Attacks
Mobile applications have three areas of vulnerability: smartphones, data transferred, and servers. Users will store data directly on their phones, but most are stored on servers. When the user requests, the data is accessed only after proper identification. Data is transmitted to the smartphone from the server or vice versa. But what if someone could intercept this data?
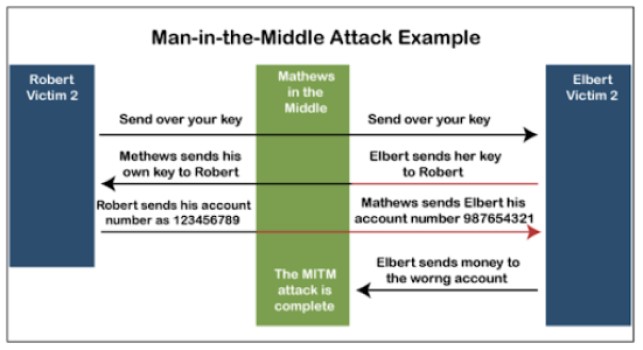
Source: Javapoint
In the past, Man-in-the-Middle (MITM) attacks only happened on web pages. As hackers become proficient, MITM attacks can also occur in mobile apps. In MITM attacks, attackers intercept and manipulate mobile app data to obtain sensitive information.
MITM attacks work well because:
- Users are often indifferent to the numerous permissions, agreements, and confirmations required.
- Users download and install too many untrusted mobile apps.
- Many users use their phones for both personal and professional purposes.
8 Best Practices for Securing User Data in Mobile Apps
The BYOD (Bring Your Own Device) trend is famous for a reason. It happens because employees are vulnerable targets for cybercrime. They mix personal and professional data in one device. Implementing additional measures to safeguard sensitive data in mobile apps is always advisable.
1. Data and Code Encryption
Minor coding errors or oversights in testing can leave room for bugs. It leaves mobile apps vulnerable to exploitation by hackers. One way to overcome this is to use encryption.
There are two ways to encrypt; code and data encryption. Code encryption converts the text into a series of numeric codes. It renders data incomprehensible to users, thereby protecting user data. Meanwhile, data encryption converts data into numeric code, making it unreadable to hackers. There are two data encryptions; symmetric and asymmetric. Symmetric encryption employs the same key for encryption and decryption, while asymmetric encryption uses a distinct key.
2. Perform a thorough security check
Before launching a mobile app, check its functionality and security. The goal is to detect the vulnerability of the application. Regular testing is recommended, even after the app has been launched.
Sometimes, the developer's team may rush app testing to meet a launch deadline. Even though app vulnerabilities can threaten user security. Here are the steps a developer can take to check app security:
- Conduct code audits and tests to ensure flawless authentication and authorisation procedures.
- Utilise an operating system emulator to test the mobile app's performance.
- Verify access control to identify any data security gaps.
3. Secured Codes
IT Pro Portal shows that 82% of mobile app vulnerabilities are caused by code. It shows that the code needs extra security. Developers should ensure that the source code is bug-free before debugging.
Understanding the application architecture or hiring an application designer can be the best step to secure the application. They will test the app from various angles and ensure the code is secure. Additionally, protecting the backend servers from malicious cyber attacks is equally important.
4. Secured Data Storage
Many developers underestimate the importance of secure data storage. They must ensure that no sensitive data is shared with: application logs, third parties, PPI mechanisms, and keyboard caches. Mobile app code and data should not be stored in another web application. Users can activate the automatic delete feature, which deletes data after a certain period.
Here are some steps you can maximise to secure data storage:
- Encrypt all files and databases with an SQL server or keychain.
- Use dynamic analysis to record data.
- Secure data in transit using a VPN (Virtual Private Network), SSL (Secure Sockets Layer), or TLS (Transport Layer Security).
5. Secure APIs
APIs are the primary means for data to flow between applications, the cloud, and users. When developers use third-party APIs, they must ensure the code's security. Limit API access with data authorisation to only access the required applications. Here are some steps to secure the API:
- Use a gateway to protect the API.
- Implement a central OAuth server to handle user authentication securely.
6. High-level Authentication
Design the mobile app to prompt users to change their password regularly. Plus, provide features like alphanumeric passwords. It establishes a layered authentication process and improves overall security.
In sensitive apps such as banking, use an extra layer of security. Developers can add features for retina scanning or biometric authentication. Both of these features are high-level authentication which is almost impossible to breach. Additionally, using an OTP (one-time password) is another effective way to secure the app.
7. Bring Your Own Devices Policy
Remote workers may be familiar with the BYOD trend. It is the trend of using personal devices for work. However, BYOD can make it difficult for IT teams to track data movement or manage data access. Organisations can invest in Mobile Device Management (MDM) products to help with application security.
8. Just be careful
Apart from developers and companies, users must also protect their data. Companies can provide training to educate about the importance of data security. Or give an appeal to employees to:
- Only download apps from trusted sources.
- Create passwords with solid combinations.
- Enable auto-exit feature on sensitive mobile apps.
Conclusion
Mobile application security becomes more crucial as the number of smartphone users increases. However, this also means an increased risk of fraud and hacker attacks. Therefore, users, developers, and organisations must prioritise security measures in mobile applications. The best practices mentioned above can help address concerns about mobile application security.


