
Managing web app sessions is essential for developing secure and reliable web applications. It allows users to interact with the website securely, ensuring active sessions.
Have you ever had to log in again, even though you've logged in before? Web applications use re-authentication to ensure account security, but it's not the best solution. Effective session management helps users stay secure without constantly logging back in.
OWASP identifies improper authentication as the second biggest risk for application security. An authorisation is often exploited in several hacks, including:
- Gitlab is susceptible to brute force attacks and authentication token vulnerabilities due to its short duration.
- Meta released a security update after 90 million Facebook accounts were affected by token theft.
Web application session management is difficult, expensive, and time-consuming. A16z and former CSO Box mentioned that authentication and authorisation are the biggest security expenses for organisations.
What exactly is session management? How does it work? Why is it expensive to implement in web apps? This article will delve deeper into session management.
The Definition of Session Management
Session management refers to the user's interaction with a web app. Its processes enable secure access to information without re-authentication. The session is typically divided into two; short-lived and long-lived.
Long-term sessions keep the user logged in to the application. The device will store the ID so the user can access the app without re-login. Short-term sessions are designed to expire when the user exits the app. Whenever they close the app, they must log in again.
Both types of sessions have drawbacks. Long-term sessions are more vulnerable to account hacking, while short-term sessions are more complicated.
How Session Management works
During the interaction, user information is transferred between the server and browser and then saved or processed by the browser. Session management implementation involves three functions: The session ID, cookie storage, and expiration date.
1. Session IDs
When a user first logs in to the web app, the server generates a unique session ID linked to the user. But for every new request, the server needs a way to identify the authentication request. Then, the cookie is created and sent with the new request activity.
2. Session Cookies
Besides generating session IDs, the server generates cookies stored in the user's browser. The cookie's content is sent with each new request, so the server understands that the request comes from a single user.
3. Session Expiry
A session is a temporary state of a specific period. Even if the app uses long-term sessions, sessions can expire if the user hasn't interacted for weeks. The cookie containing the session ID is automatically deleted when the session ends.
Threats and Cyber Attacks
As mentioned earlier, managing sessions on web apps aim to maintain user data security. Poor session management can be a threat to application security.
1. Session Fixation
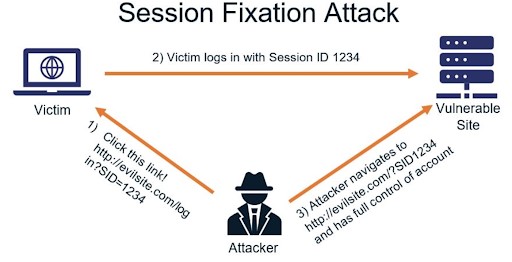
Source: Security Boulevard
Session fixation exploits weaknesses in browser authentication and poor session management. The attacker logs in using a specific session ID to impersonate the origin user and use the credentials to log into the account. The difference between fixation and hijacking lies in the session ID used.
2. Session Hijacking
A brute-force attack can occur if the cookie used to store the session ID is not secure. Hackers can spoof session IDs, impersonate users and take over accounts. This activity is known as session hijacking, which results in the loss of information in the application account.
3. Session Expiry Too Long
When the website does not set a certain period, cookies can last forever in the browser. These cookies make accounts vulnerable and easy to access. Developers sometimes create long cookie periods to make it easier for users, but that can be a security threat.
4. Physical Access
Physical access attacks are common on public computers and can occur in two ways. First, attackers can easily read cookies through application pages. Second, hackers can steal the authentication token after the user exits the application.
5. Database Access
This threat often occurs in companies with high growth, such as startups. Hackers who manage to access the database system have the potential to get an active authentication token. As a result, hackers can hijack sessions and easily access information.
Managing Web App Sessions Securely
Having many vulnerable points with attacks is bad for web applications. Here are some ways to implement secure session management:
1. Session ID properties
Developers can configure session ID properties which are useful for preventing attacks. For example, set the minimum session ID length is 128 bits with a unique combination. The ID must be unpredictable and not descriptive of user information. The 128-bit value is a reference, not the absolute minimum value.
2. Attributes of cookies
Cookies have different attributes that can enhance the security of session IDs exchange. These attributes include:
- Secure: This attribute instructs the browser to transmit the cookie over encrypted HTTPS connections, ensuring the cookie is not sent over an insecure network.
- HttpOnly: It tells the browser not to disallow JavaScript access to cookies. It's to prevent malicious scripts from stealing code.
- SameSite: Cookie settings can be strict or lax. Strict cookies are sent with the same site request. In contrast, lax cookies are sent with cross-site requests.
- Expires: This is a sign that cookies are persistent and will be stored by the browser until they expire.
3. Generation of new Session IDs
Throughout the interaction process, session IDs cannot be the same. It has to be updated whenever user privileges change. For example, regenerate the ID when a user logs in to their account so that the session ends when the account is inactive for a certain period.
4. Limit the number of sessions per user
The web application must provide a user session threshold or quota. Use lots of data to determine the number of user sessions per account. For example, an online banking service may set a limit on daily logins.
5. Revoke the session
This practice automatically revokes a suspicious-looking user's session. For example, one account uses two logins by the same official user but in different places, one from Bangkok and one from London. These activities differ only a few minutes and use other devices.
Conclusion
The control and implementation of session management in web applications should be taken seriously by enterprises. It is not limited to local or global service provider organisations. Device developers should implement best practices, so that session management is clean from threats.
By working with VirtualSpirit, business owners can take advantage of their expertise and experience in developing web applications with robust security features. You can rest assured that your web app sessions are managed securely. Contact us now!




